You and I are pirates, or what you can and cannot download from the Internet. Definition of selflessness Back up messages on your phone
As a rule, over time, a huge amount of text messages, both received and sent. It can be just text SMS or multimedia messages containing photos and videos.
What to do if the user decided to buy for himself new phone, but at the same time wants to save all SMS? In this case, it is possible thanks to the flexible settings of the Android operating system.
Navigation on the page:
What is the difficulty of the task?
If the usual copying of data, for example, files and folders in the Android operating system is carried out in a few clicks, and this does not require installation additional programs, then with messages it will be a little more difficult. However, as practice shows, the entire list of actions described can be performed by an ordinary user without any problems!
The transfer of messages is possible only through specialized applications, of which, fortunately, in the service from Google there are quite a few. We will consider several options in this article.
Copy messages by branded applications
Many popular manufacturers have released their own special software to solve this problem. If you did not find the name of your gadget in the list below, then we recommend that you go to the next section of our article, which describes universal application SMS Backup & Restore. It can work on most mobile devices.
- Motorola
- Samsung
- Sony
Developers from HTC Corporation have created their own software, which allows you to copy and transfer SMS from one Android device to another. This is about hTC app Transfer Tool. With the help of this program, the user can transfer not only messages, but also calendars, notes, contacts and much more from one device to another in a few clicks. The only drawback of the app is that it only works on HTC smartphones!
LG has an app called LG Backup. With this tool, you can transfer almost any type of data, from calendars and messages to multimedia data. Only a smartphone that receives data must have Android Jellybean or higher installed.
Motorola has Motorola Migrate for Android, which is designed to transfer SMS and other data from one device to another. Again, the disadvantage of the application is that only devices from this manufacturer are supported.
Now let's move on to Samsung devices! The large giant pleases its customers with its own application for transferring messages, settings, records and other data. Samsung program Smart Switch is distributed in the service Google play free of charge and can be installed on most devices from this manufacturer. It is also possible to support work with iPhone devices.
Sony developers recently released own program Xperia Transfer Mobile for copying and transferring data. It works not only with Xperia devices but with others mobile phones... Almost all mobile operating systems are supported, namely: Android, iOS, Windows Phone... It is possible to transfer not only text, but also multimedia messaging, settings, photos and videos, notes and other important information.
The universal way - how to copy messages with SMS Backup & Restore
The SMS Backup & Restore application was developed with only one purpose - to copy and transfer SMS from one phone to another for Android. If you do not want to waste time once again trying to understand the principle of working with one or another program described above, then install this application. Here, all operations are performed in a few clicks, regardless of the smartphone manufacturer and OS version.
Versions 1.5 to 5.0 and higher are supported. The developers are constantly releasing updates and fixing bugs.
And so, to work you will need to do the following:
- Go to the Google Play service and download the application to your device.
- Allow installation and wait for the installation to complete. Run the program.
- Click on "Backup" to create a complete copy of all messages on your phone.
- Throw off the finished copy to another smartphone and go to the program. Find the item "Restore" there and specify the path to the file. Within a few minutes, the application will restore all your messages, with complete list contacts, attachments.
The application is distributed only with support for a foreign language, but an ordinary user can easily use it, since there are only a few menu items in the interface:
- Backup - make a copy of messages.
- Restore - restore a copy of messages.
- Delete Backups - delete all copies of messages.
- Delete Messages - delete all messages.
If you have many copies, then you can use the built-in search, which is able to find all copies in the Android operating system in a matter of seconds. There are also settings for users in the application itself! Files can be saved in XML and uploaded to cloud servicesfor example from Google or Mail for further work.
All messages can be viewed on a personal computer, edit the content, view information about the sender. It is also possible to set up automatic copying at a scheduled time, for example, every week.
And so, now you know how to transfer SMS from Android to Android, using various programs and tools that are available in free google mode Play! Do not forget to regularly create not only copies of messages, but also contacts, and preferably android settings... You can read instructions about this on our website!
According to various estimates, from 50 to 95% of all emails in the world are spam from cyber fraudsters. The purposes of sending such letters are simple: infect the recipient's computer with a virus, steal user passwords, force a person to transfer money “to charity,” enter his bank card details or send scans of documents.
Spam is often annoying at first glance: a crooked layout, automatically translated text, password entry forms right in the subject line. But there are malicious letters that look decent, subtly play on a person's emotions and do not raise doubts about their veracity.
The article will talk about 4 types of fraudulent emails that are most often sent to Russians.
1. Letters from "government organizations"



Fraudsters can pretend to be the tax authorities, the Pension Fund, Rospotrebnadzor, the Sanitary and Epidemiological Station and other state organizations. For persuasiveness, watermarks, scans of seals and state symbols are inserted into the letter. Most often, the task of criminals is to scare a person and convince him to open a file with a virus in the attachment.
Usually it is a Windows ransomware or blocker that disables the computer and requires you to send a paid SMS to resume work. A malicious file can disguise itself as a court order or a summons to the head of the organization.
Fear and curiosity turn off the user's consciousness. On accountant forums, there are cases when employees of organizations brought files with viruses to their home computers, because they could not open them in the office because of the anti-virus.
Sometimes scammers ask to send documents in response to a letter in order to collect information about the company, which will be useful for other deception schemes. Last year, a group of scammers was able to trick a lot of people into using a “request to fax papers” distraction.
When an accountant or a manager read this, he immediately cursed the tax authority "There are mammoths sitting there, e-mine!" and switched my thoughts from the letter itself to solving technical problems with sending.
2. Letters from "banks"


Windows blockers and ransomware can hide in fake letters not only from government agencies, but also from banks. The messages “They took a loan in your name, read the lawsuit” can really scare and cause a great desire to open the file.
Also, a person can be persuaded to enter a fake personal Area, offering to see the accrued bonuses or to receive the prize that he won in the "Sberbank Lottery".
Less often, scammers send invoices to pay service fees and additional interest on a loan, for 50-200 rubles, which are easier to pay than to understand.
3. Letters from "colleagues" / "partners"

Some people get tens business letters with documents during the working day. With such a load, you can easily take the "Re:" tag in the subject line and forget that you haven't corresponded with this person yet.
Especially if in the field the poisoner indicates "Alexander Ivanov", "Ekaterina Smirnova" or any simple Russian name, which absolutely do not linger in the memory of a person who constantly works with people.
If the goal of the scammers is not to collect SMS payments for unlocking Windows, but to harm a specific company, then letters with viruses and phishing links can be sent on behalf of real employees. The list of employees can be collected in social networks or viewed on the company's website.
If a person sees in a mailbox a letter from a person from a neighboring department, then he does not particularly look at it, he may even ignore the antivirus warnings and open the file no matter what.
4. Letters from Google / Yandex / Mail
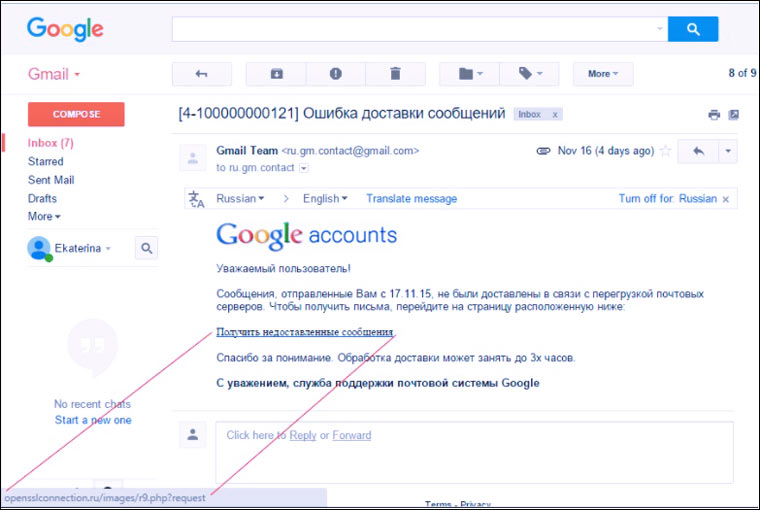

Google sometimes sends letters to the owners of Gmail inboxes that someone tried to log into your account or that they ran out of space on Google drive... Scammers successfully copy them and force users to enter passwords on fake websites.
Users of Yandex.Mail, Mail.ru and other postal services also receive fake letters from the "service administration". Standard legends are: "your address has been added to the black list", "the password has expired", "all letters from your address will be added to the spam folder", "look at the list of undelivered letters." As in the previous three points, the main weapons of the criminals are the fear and curiosity of the users.
How to protect yourself?

Install an antivirus on all of your devices to automatically block malicious files. If for some reason you do not want to use it, then check all at least slightly suspicious email attachments on virustotal.com
Never enter passwords manually. Use password managers on all devices. They will never offer you password options to enter on fake sites. If for some reason you do not want to use them, then manually enter the URL of the page on which you are going to enter the password. This applies to all operating systems.
Wherever possible, connect password confirmation via SMS or two-factor identification. And of course, it is worth remembering that you cannot send scans of documents, passport data and transfer money to strangers.
Perhaps, when looking at the screenshots of the letters, many of the readers thought: “Am I a fool to open files from such letters? For a kilometer you can see that this is a setup. I won't bother with a password manager and two-factor authentication. I'll just be careful. "
Yes, most fraudulent emails can be exposed by eye. But this does not apply to cases where the attack is directed specifically at you.
The most dangerous spam is personal

If a jealous wife wants to read her husband's mail, then Google will offer her dozens of sites that offer the service "Hacking mail and profiles in social networks without prepayment."
The scheme of their work is simple: they send a person high-quality phishing emails that are carefully composed, neatly laid out and taken into account. personal characteristics human. Such scammers are genuinely trying to hook a specific victim. Find out from the customer her social circle, tastes, weak points. It can take an hour or more to develop an attack on a specific person, but the effort pays off.
If the victim comes across, they send the customer a screen of the box and ask him to pay (the average price is about $ 100) for their services. After receiving the money, they send a password from the box or an archive with all letters.
It often happens that when a person receives a letter with a link to the file "Video compromising evidence on Tanya Kotova" (hidden keylogger) from his brother, he is filled with curiosity. If the letter is provided with text with details that are known to a limited circle of people, then the person immediately denies the possibility that the brother could be hacked or someone else is pretending to be him. The victim relaxes and fucking disables the antivirus to open the file.
Not only jealous wives, but also unscrupulous competitors can turn to such services. In such cases, the price tag is higher and the methods are thinner.
You should not rely on your attentiveness and common sense. Just in case, have an emotionless antivirus and password manager backing you up.
P.S. Why do spammers write such stupid letters?

Carefully crafted scam emails are relatively rare. If you go to the spam folder, then you can have fun from the heart. What kind of characters are not invented by scammers to extort money: the director of the FBI, the heroine of the TV series "Game of Thrones", a clairvoyant who was sent to you by higher powers and he wants to tell the secret of your future for $ 15 dollars, the killer to whom you were ordered, but he mentally offers to buy off ...
An abundance of exclamation marks, buttons in the body of the letter, a strange sender's address, an unnamed greeting, automatic translation, gross errors in the text, an obvious overkill of creativity - letters in the spam folder simply “scream” about their dark origin.
Why do scammers who send their messages to millions of recipients not want to spend a couple of hours composing a neat letter and spare 20 bucks for a translator to increase audience response?
In a Microsoft study Why do Nigerian Scammers Say They are from Nigeria? the question “Why scammers continue to send letters on behalf of billionaires from Nigeria, when the general public has known about“ Nigerian letters ”for 20 years is deeply analyzed”. According to statistics, more than 99.99% of recipients ignore such spam.
Selflessness is one of the best moral qualities. An unselfish person does everything for others and does not demand a reward for this work. It seems to me that in our today's world, where money reigns, it is very difficult to find such a person who is ready to come to the rescue at any moment and do something good and useful completely free of charge. Now almost everyone is worried about material goods and no one wants to spend mental and physical strength on something that will not bring them profit.
People at all times have encouraged unselfishness. Even though she herself was not like that, she admired those who were. Russian and foreign writers in their works also rewarded their best heroes with this important moral quality, showed how the character seeks to help other people.
In my opinion, the most striking example of disinterestedness is the actions of Danko from Maxim Gorky's story "The Old Woman Izergil". The character sacrificed his heart to save lives. This disinterested act is worthy of at least respect, because the hero destroyed himself in the name of a just cause. But people didn't appreciate it.
Opposed to Danko Larra, who only cares about himself. He is cruel, having lost kindness, mercy and responsiveness. This character's only desire is to become free from society. He would never sacrifice himself for salvation. His soul did not find a refuge, so Larra's shadow constantly walks along the steppe and instills fear in its inhabitants. And people remember Danko only during a thunderstorm.
Maxim Gorky insists that there is no need to go to extremes and be only disinterested or only selfish. In life, there is only black and white colors, there are other shades. But if you want to remain in human memory for many years and centuries, you need to do only good deeds and not demand rewards for them.
A sufficient number of unselfish people know history. People do not forget their heroes, they carefully honor the memory of them. Writers speculated about the origin of selflessness and indifference. If you look at it, then unselfish people live much more difficult: they have a duty and principles that cannot be backed down. Still such people are not appreciated during their lifetime. But sooner or later they will become a legend and new generations will certainly imitate them.
To be an unselfish person means helping other people anytime, anywhere, at any time of the day or night, and not demanding a reward for it. A person with unselfishness knows how to love, compassion and pity. You should strive for such qualities all your life.
Hello. Today I will tell you about another interesting thing that will help you make a full backup of SMS messages on your smartphone or tablet. I will say right away that this backup guide will only work for those devices that run the Android OS.
No one can predict what will happen in a day, hour, minute. This also applies to the security of data stored on your mobile devices. If the information is very important and may be required at some time, then it is necessary to take a responsible approach to the issue of the correct storage of data - you need to do backup... The capabilities and resources of this operating system allow you to effortlessly backup almost any information on the device. This can be represented by contacts, photos, videos and, of course, sms.
Sensing the need of users for this function, the developers began to develop some specialized applications that can backup SMS on Android. The official store has a huge number of similar programs. They all perform the same function, but the result is achieved in different ways. Some work only at the expense of the Internet, while others can do it all off-line. What will be convenient for you, decide for yourself. I think it is worth providing an overview of these applications that will help you with backups.
SMS Backup & Restore
The first application we'll talk about will be. This is a fairly popular application that has already received over 1 million downloads and has earned a lot of positive reviews. All this proves that the program really works and will be able to cope with the task at hand.This application backs up SMS messages in xml format. Do not be afraid that the format is completely unfamiliar. Let's continue. The copied information can be moved to any device with Google operating system, the firmware version doesn't matter. In addition to mobile devices, the file can be downloaded to an ordinary personal computer, where you can read the texts of the copied sms. Keep backup files you can on your memory card or send yourself not email... In addition, you can use services for storing files: Dropbox and. By the way, I almost forgot. The application cannot work with messages that contain graphics. These are mms.
Super Backup: SMS & Contacts
Let's talk about the next application developed by Mobile Idea Studio called. I think it's not worth describing the main functionality of the application, we'll just spend more time. I will only point out the main advantages and differences from the previous one.With what this program better from the previous one? That's what. Backup: SMS & Contacts can work not only with SMS, but also with the phone book, calendar and call list. In general, the list of items has become larger. If you want to make a comprehensive backup of all device data, then you can use this application. By the way, here you can set a specific time for copying. This is also available in the previous application.
I think this will be sufficient. More is not needed. Carefully read each of the above applications, choose the best. Only after that it will be possible to start the SMS backup process. Thanks.
Engineering and Science >> Computer and Internet
"Partner" No. 4 (127) 2008
You and me are pirates, or what you can and cannot download from the Internet
S. Muchnik (Dortmund)
Downloading from the Internet is expensive
The real pirates at least knew why they would be hanged on the yard. We, modern ones, are completely unprepared for an invitation to the scaffold, and the polite request of the law firm to pay a certain amount of thousands (!) Euros for our (more often - our children) disinterested love for culture, in particular, for cinema and music, plunges us in shock. But more often than not, we have to pay, and what is even more offensive, we pay not only the music and video industries for the illegal use of their products, but also those lawyers who are looking for us and fining us.
As the RTL channel told at the end of February, in Hamburg, for example, 98 employees of one company are only engaged in catching music pirates and quite successfully: at least a hundred a day.
If you want to sleep well, then forget about the Internet as a source of illegal videos, music, programs and games. Buy it all at the store, go to the movies or borrow movies from the video library, listen to music from friends or on the radio. For most, these advice sounds a little wild: why is there high-speed Internet, DSL-Flatrate, burners and programs that bypass copy protection? In a word, "Tired of talking and arguing ... in the filibuster far blue sea ...". This means that you do not need to be surprised or offended, but rather calculate how much legal good you could buy for those two, five or ten thousand euros for which you will be fined.
Or do you hope that they will not be fined, will not get there? Perhaps, because last year, copyright infringement cases (music, films) were initiated “only” against 60 thousand Internet users in Germany.
Piracy technology
The technology of piracy is associated with so-called peer-to-peer networks (P2P, short for Peer-to-Peer), which allow users to exchange their files uncontrollably and often without intermediaries. It all started in 1999 with the idea of \u200b\u200ba student named Napster, Sean Fanning, who organized the first centralized, that is, with a central server, file sharing service under the same name. This was the beginning of the avalanche, for although Napster was banned by the court, many other completely decentralized file hosting services (Tauschbörsen) arose.
User installs special program, and there are many of them now, for example Bit Torrent, Azureus, Emule, Lime Wire, Shareaza, eDonkey, Bearshare, Kazaa. Each one is legal and free and issues a search request desired filesuch as the newest MP3 song. At the same time, he makes his musical (video, book, software) stocks available to everyone. The program finds what you are looking for, according to the request, and starts downloading a music file, while other file sharing partners download your files. The whole planet is involved in the exchange process, everything is anonymous, you don't need to know the language, everyone is happy ...
Everything except the music and film industries. Judge for yourself: the turnover of the German music industry was 2.75 billion euros in 1997, and in 2005 it was one billion less. It is estimated that the potential loss of turnover in 2006 was € 6.35 billion, with illegal disk copying accounting for € 5.95 billion and Internet piracy “only” half a billion. And the porn industry is suffering!

The process of catching pirates
Everything would be fine for pirates, if not for one clue - the dynamic IP-address of his computer, assigned anew each time he logs on to the Internet, by which each user can be identified. This is the thread by which the inexorable Themis is pulling.
The process of catching and punishing a computer pirate goes something like this.
First, the suspect is identified (by the same firm in Hamburg or another). Then his provider, for example, Telecom, Arcor "y or 1 & 1, is sent a request to save information for further investigation, then a complaint is filed against an unknown attacker to the prosecutor's office, which immediately asks the provider for the coordinates of the criminal owner of the Internet connection (some compare the IP address to a fingerprint ).
After that, the prosecutor's office, as a rule, transfers this data to the law office, which sends the pirate Abmahnung with a listing of the corpus delicti and the demand for monetary compensation for copyright infringement and the remuneration of a lawyer.
The amount may be quite modest - up to a thousand euros, but it may also be such that you will have to urgently sell the car.
In the United States, one user of the Kazaa program was fined $ 220,000; in Europe, they are fined more moderately. They also take into account, although this is not clearly prescribed, the number of songs on your hard disk (MP3 files), a lot or not. 1000 songs is already a lot, which means you are a particularly dangerous pirate. In addition, the Unterlassungserklärung is also required of you - an oath promise never to engage in piracy again.
By the way, in some, especially vicious cases, a home search, and confiscation of a computer, and imprisonment by court for up to three years is not excluded.
There are lawyers who specialize exclusively in the pursuit of video and music pirates, but there are (just in case, keep in mind) others who undertake, if not completely to protect from the former, then at least minimize losses. However, it is better not to know either one or the other.

And from this year on, the pirates will have no life at all.
The new Copyright Law "Zweite Gesetz zur Regelung des Urheberrechts in der Informationsgesellschaft" has been adopted. And if earlier it was not criminal storage or downloading from the Internet, but only their distribution, provision, albeit disinterested, to others, now all participants in exchange operations are outlawed. Moreover, now downloading not only through P2P networks, but also from websites, is also considered illegal.
You go, say, to a Russian-language site, to some "Captain Nemo" or "World of Books", and download an American film that interests you, which has not yet been released in Europe and on screens. And this is now a crime. The same applies to books, music, photos, even TV series. You yourself have to guess what is "offensichtlich rechtswidrig", that is, "obviously illegal", and what is still permissible.
Moreover, all commentators of the new text of the law recommend, in doubtful cases, to make a decision in favor of refusing to download, for their own safety. Many sites, mostly foreign, including Russian-language ones, offer accelerated and unlimited downloads for little money - this, mind you, has nothing to do with legal buying on the Internet. You simply pay for the quality and speed of receiving the illegal product.
There are, for example, the well-known servers Rapidshare, DepositFiles, Megaupload, Filefactory and many other so-called One-Click Hosters, from which you can download anything for free or inexpensively, but comfortably. Download links, again free of charge, are provided by all kinds of sites, and the files themselves for downloading are selflessly uploaded to Rapidshare & Co by enthusiasts, fighters against greedy music and film companies, and publishers. At the end of the chain there is a consumer of this illegal product, who pays nothing or pays little to the wrong, i.e. you, a pirate worthy of punishment and public censure.
Besides the Internet, is it possible to copy music and video discs?
Just for yourself or for friends? Here the law seems to be softer: if it is for personal use and in small quantities (up to 7 pieces), then it can be copied, unless, of course, the discs have copy protection, it is forbidden to bypass it. And by the way, the copyright for songs is preserved for at least 50 years, so you are unlikely to legally acquire an unprotected CD or DVD with a new product.
There is also streaming video (Stream), when you do not download a movie from the Internet, but simply watch it on the monitor, which has become quite possible at high speeds of the DSL connection. Here, even the commentators of the law do not have complete clarity: on the one hand, you do not download anything and nothing is saved on the computer, on the other hand, you still watch the new American thriller not in the movies and for money, but at home and for free; here, according to the letter of the law, one should, alas, abstain.
And finally, analog copies from digital (digital) carriers, even protected ones, are not prohibited. That is, you can transfer a movie from a DVD to a videotape. But, of course, for personal use and, of course, downloading an analog copy or displaying it on the Internet is prohibited.
According to the latest data, the number of illegal downloads in Germany has dropped significantly. So, in 2007, 312 million songs were downloaded, and a year earlier - 374, which is associated with the tightening of the fight against music pirates. Every second German burns CDs or DVDs legally, within the limits of the copyright for personal use. Moreover, if in 2006 766 million blank disks ("discs") were used, then in 2007 - only 685. According to the same data, since 2007, the number of legal operations with musical works exceeded the number of illegal ones.
Finally, not all music on the Internet has a criminal connotation. Here is the first legal site for exchanging music via P2P, called




